- Home
- /
- SAS Communities Library
- /
- SAS Viya SAML Easy Azure Setup
- RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
SAS Viya SAML Easy Azure Setup
- Article History
- RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
SAS is working in partnership with Microsoft to improve the customer experience around different areas of the configuration of SAS Viya. In December 2023 a notable result of this was the publishing of a Microsoft Entra Gallery application for the configuration of SAML authentication with SAS Viya. In this post we’ll look at the new Microsoft Entra Gallery application and see how it can be used.
Using the Azure Portal
The configuration of SAS Viya to use Microsoft Entra ID as the SAML Identity Provider is covered in the SAS Viya Platform Administration guide. Microsoft has some high-level documentation, but far more detail is provided in the SAS documentation. Prior to December 2023 you would need to add a non-gallery application when configuring Microsoft Entra ID as the SAML Identity Provider. Now when you add the Enterprise Application you can search for SAS Viya in the gallery. This will return the following:
Select any image to see a larger version.
Mobile users: To view the images, select the "Full" version at the bottom of the page.
When you select this the following options for creating an instance of the Microsoft Entra Gallery application will be shown:
You just need to provide a name for your instance of the Microsoft Entra Gallery application and then you can create it.
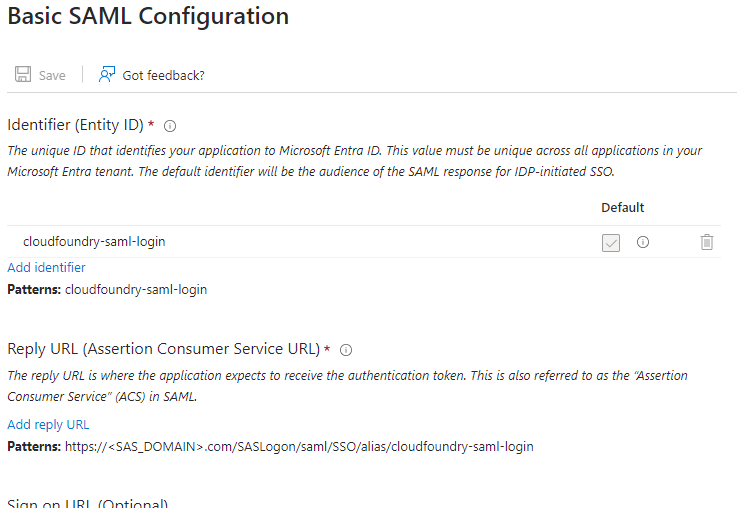
Once the application instance is created. Under the Enterprise Application, select Set up Single Sign-On with SAML to proceed with providing the details of your SAS Viya environment. In the Basic SAML Configuration section shown here:
You need to provide:
- Identifier (Entity ID) – notice that using the Microsoft Entra Gallery application means that the SAS Viya default value is already populated, but this can be changed to something meaningful for your environment.
- Reply URL (Assertion Consumer Service URL) – this is the URL to your SAS Viya environment and the Patterns provides an example of what that should look like. It includes the Entity ID at the end of the URL.
You can provide:
- Relay State – this will be the relative URL to any SAS application, for example /SASDrive/, and will be used in the Identity-Provider Initiated SAML Authentication Flow.
- Logout URL – this will enable you to have single logoff.
You can then continue with the rest of the configuration as per the SAS documentation.
Using the Azure CLI
The same steps we have discussed doing in the Azure Portal can also be done using the Azure CLI. To be able to add an instance of an application from the Microsoft Entra application gallery into your directory you need to know the globally unique applicationTemplate-id. You can find the applicationTemplate-id using the Microsoft Graph explorer and searching for SAS Viya. For example, the URL:
will return details of the SAS Viya Microsoft Entra Gallery application template.
Then as per the Microsoft documentation we can instantiate an instance. The following, Linux-based, example code will create the Enterprise Application in our tenant:
myAppReg=$(az rest --method post --url https://graph.microsoft.com/v1.0/applicationTemplates/$myAppTemplateId/instantiate \
--body "{\"displayName\": \"${myDisplayName}\"}") ;\
myAppId=$(echo ${myAppReg}|jq -r '."application"."appId"') ;\
myId=$(echo ${myAppReg}|jq -r '."application"."id"') ;\
mySPId=$(echo ${myAppReg}|jq -r '."servicePrincipal"."id"') ;\
while [ "$(az ad sp list --display-name ${myDisplayName} --query '[].id' -o tsv|wc -l)" -lt "1" ]; do echo "Waiting for Service Principal to be created...";done ;\
az rest --method patch --url https://graph.microsoft.com/v1.0/servicePrincipals/${mySPId} --body "{\"preferredSingleSignOnMode\": \"saml\"}"
Within this example code, we need to provide the $myAppTemplateId which we found earlier from Microsoft Graph Explorer. Also, we provide ${myDisplayName} as the custom name of the instance of the Microsoft Entra Gallery application.
The last part of this code will also enable SAML as the mechanism for Single Sign-on. This is the action we performed in the Azure Portal by selecting Set up Single Sign-On with SAML.
However, when using the Azure CLI, it does not setup a token signing certificate automatically. Instead, we can use the following code to do that:
myExp=$(date -d "+3 years" +%FT%TZ)
myCert=$(az rest --method post --uri https://graph.microsoft.com/v1.0/servicePrincipals/${mySPId}/addTokenSigningCertificate \
--body "{\"displayName\":\"CN=SASViya\",\"endDateTime\":\"${myExp}\"}") ;\
myThumbPrint=$(echo ${myCert}|jq -r '."thumbprint"') ;\
az rest --method patch --uri https://graph.microsoft.com/v1.0/servicePrincipals/${mySPId} \
--body "{\"preferredTokenSigningKeyThumbprint\": \"${myThumbPrint}\"}"
Finally, we can use the following code to set the SAS Viya specific values in the Basic SAML Configuration:
az rest --method patch --uri https://graph.microsoft.com/v1.0/applications/${myId} \
--body "{\"web\": {\"redirectUris\": [\"https://${logon_host}/SASLogon/saml/SSO/alias/${myEntityID}\"],\
\"logoutUrl\": \"https://${logon_host}/SASLogon/saml/SingleLogout/alias/${myEntityID}\"},\
\"identifierUris\": [\"https://${myEntityID}\"]}"
Where ${logon_host} is the hostname of our SAS Viya instance and ${myEntityID} is the Entity ID used in the SAS Viya configuration.
Optionally, use the following Azure CLI command to remove the requirement for users/groups to be assigned to the Enterprise Application before they can use it:
az rest --method patch --uri https://graph.microsoft.com/v1.0/servicePrincipals/${mySPId} \
--body "{\"appRoleAssignmentRequired\": false}"The Future
The current SAS Viya SSO Microsoft Entra Gallery application allows you to configure SAML, but it does not support SCIM provisioning. Work is underway with Microsoft to add support for SCIM provisioning to this Microsoft Entra Gallery application. This means you could use this new single Microsoft Entra Gallery application to configure both SAML and SCIM provisioning. Or you could use the new Microsoft Entra Gallery application to configure just SCIM provisioning and separately configure OpenID Connect authentication using Microsoft Entra ID.
What About OIDC
To configure SAS Viya with OpenID Connect authentication using Microsoft Entra ID you do not add an Enterprise Application, instead you use the regular App Registrations. This means that you do not need a Microsoft Entra Gallery application for the configuration of OpenID Connect.
Remember, OpenID Connect with Microsoft Entra ID also provides out-bound Single Sign-On to other Microsoft Entra ID secured resources, which is not available when using SAML with Microsoft Entra ID.
Conclusion
The SAS documentation provides you with clear instructions on how to configure SAS Viya for SAML with Microsoft Entra ID. However, in this blog we’ve just taken a closer look at the Microsoft Entra Gallery Application and seen how using it can make it easier for you to configure SAML authentication.
If you want to explore this topic in more detail, you can refer to Course: Advanced Topics in Authentication on SAS Viya.
Find more articles from SAS Global Enablement and Learning here.
Available on demand!
Missed SAS Innovate Las Vegas? Watch all the action for free! View the keynotes, general sessions and 22 breakouts on demand.
Free course: Data Literacy Essentials
Data Literacy is for all, even absolute beginners. Jump on board with this free e-learning and boost your career prospects.
Get Started
- Find more articles tagged with:
- GEL